
Instalation
I had an opportunity recently to install, update and configure UiPath RPA Orchestrator in Azure environment. Customer had a choice between setting it up in Azure VM or to deploy it as Appservice (PaaS) ARM template. Upon discussing all options, customer decided to go with PaaS option.
There is marketplace ARM template that we choose to deploy, but for this customer we had to modify it a bit within VS Code to comply with naming conventions that we developed. At time of deployment, this template installs 19.4.4 version and latest one is 19.10.15.
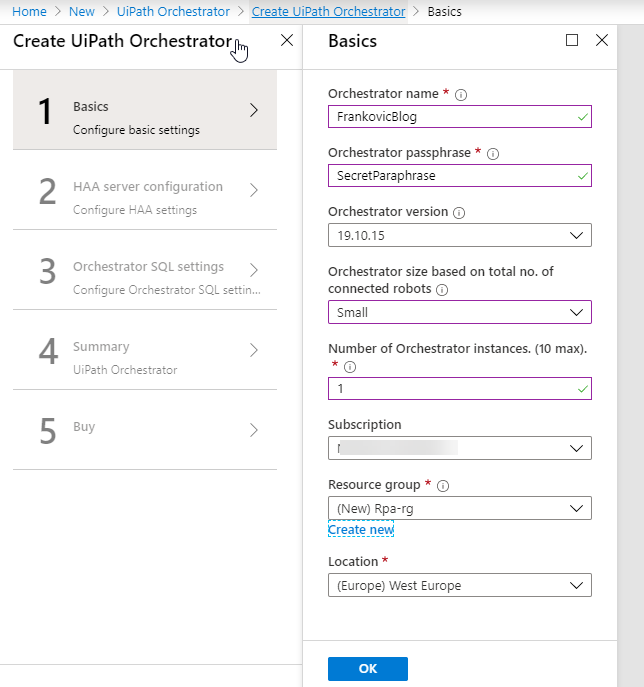
Install process is pretty much strait forward. Small instance can handle up to 100 robots and this variable is related to SQL DB (Standard S1 in this case) size which can be later on changed.
Number of instances can be modified up to a 10 and can later on also be scaled if needed. Select your Azure subscription and empty resource group or create new one.
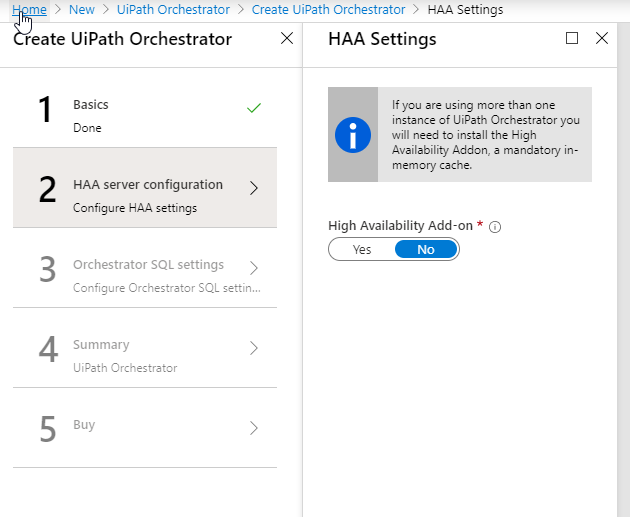
Next option is to set up HAA if you are using more than one instance of UiPath Orchestrator.
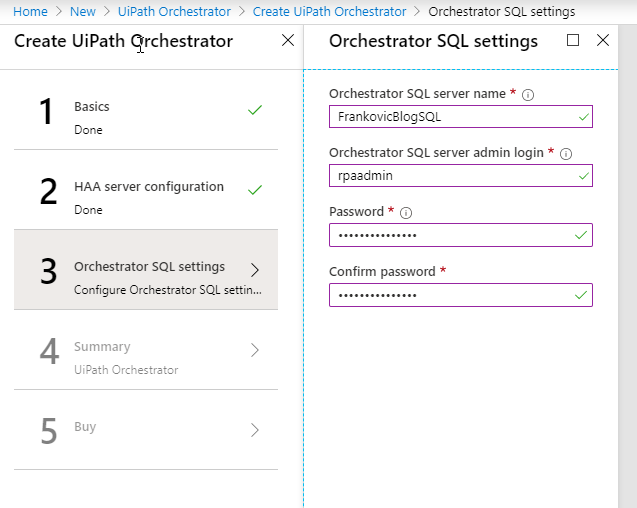
Setup SQL parameters
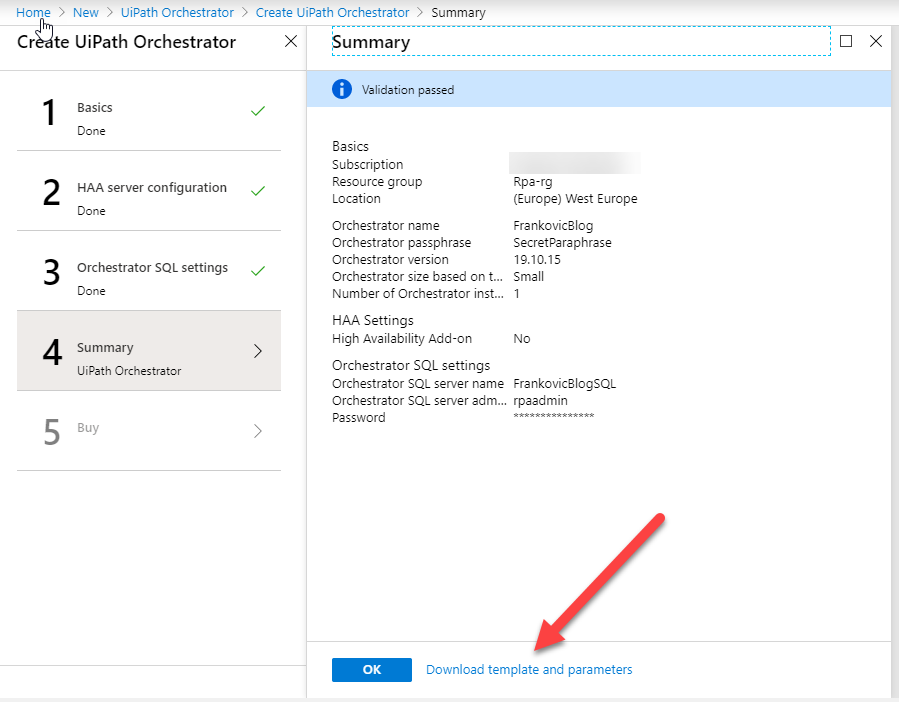
Review your setup and buy the resources.
At this point you can also download template (red arrow) and cancel deployment. Manually modify downloaded template and deploy it via PowerShell when ready. More information on manual deployment via PowerShell can be found on this link.
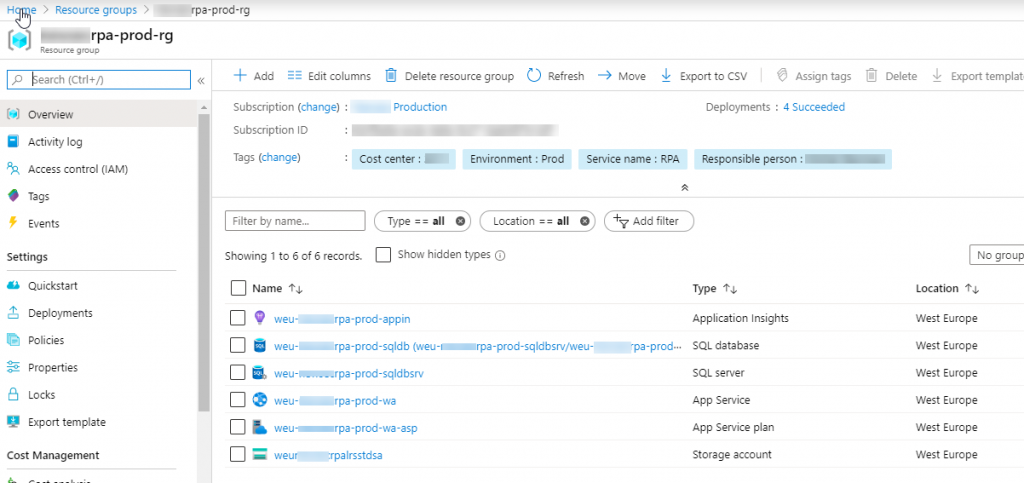
After initial deployment of the template (takes about 10 minutes to finish), several Azure resources are created
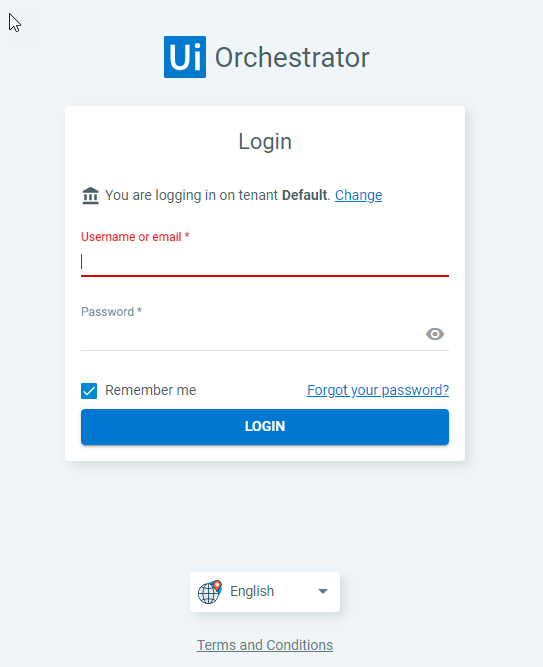
Website is up and running, and we can confirm that by connecting to provided Azure Appservice URL
Customer used default username and password to login and insert required licence. Later on, customer contacted UiPath support to obtain tenant admin and create required tenant resurces.
UiPath upgrade
Since at the time of deployment Azure ARM template contained 19.4.4. version, we did manual upgrade to newest version.
To complete this successfully, we needed to do some prerequisites in Azure:
- Register application in Azure AD
- Add applications service principal to Contributor role of resource group where app is deployed
- Create Client secret in Azure AD App registration
Detailed upgrade steps can be found in UiPath documentation.
This is sample script that we used and modified for our needs:
.\Publish-Orchestrator.ps1 `
-action Update `
-unattended `
-package "E:\Work\Orch\Setup\UiPath.Orchestrator.Web.zip" `
-stopApplicationBeforePublish `
-azureSubscriptionId "8e34be72-1937-4aa0-b70e-81bab19gbf0a" `
-azureAccountTenantId "f8350d2a-n153-4d17-8927-902c51f72797" `
-azureAccountApplicationId "$AzureApplicationId" `
-azureAccountPassword "$AzurePassword" `
-resourceGroupName "DocTest-Orch-RG" `
-appServiceName "DocTests123" `
-verboseExplanation of all script parameters can be found in documentation.
Upgrade process took about 5 minutes to complete.
Post-configuration
Additionally we have configured following settings:
- Configure custom URL for application
- Add HTTPS certificate
- Restricted IP address blocks for external access
- Azure AD identity integration
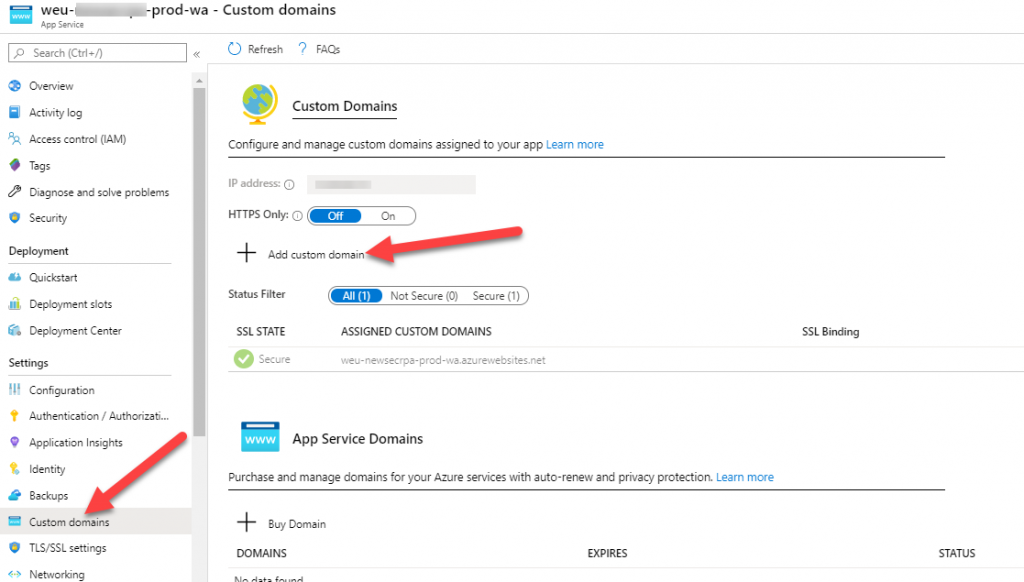
Custom URL and certificate
I would recommend to add custom URL to the app and register it with application. Later on this custom domain name can be used as URI in Azure AD application registration. Certificate for HTTPS can be added on the same page and configured additional on TLS/SSL settings pane. For this case I opted for free App Service Managed Certificates that was created and issued via Azure portal.
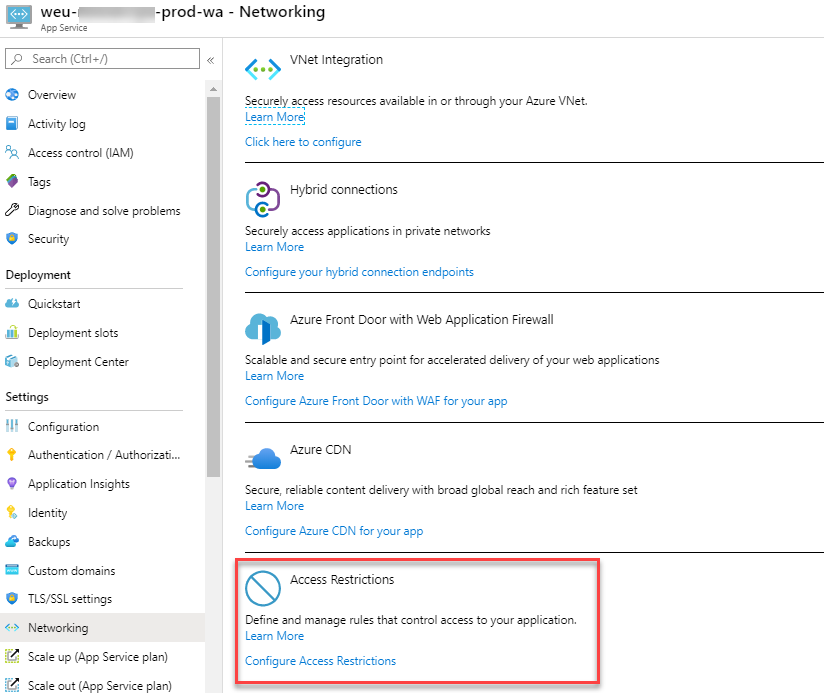
IP restrictions
Customer requires that application is available from the Internet so for initial deployment we decided to restrict access to specific IP ranges from outside. Later on we will probably add some WAF and other security solutions to the application Internet access.
Azure AD integration
More on this in my next blog post.




Hello,
I am going through the steps to perform the upgrade of Orchestrator but I’m facing the following issue when I run the script:
Add-PSSnapin : No snap-ins have been registered for Windows PowerShell version 5.
At C:\Users\Desktop\UiPathOrchestrator\Publish-Orchestrator.ps1:122 char:1
+ Add-PSSnapin WDeploySnapin3.0
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (WDeploySnapin3.0:String) [Add-PSSnapin], PSArgumentException
+ FullyQualifiedErrorId : AddPSSnapInRead,Microsoft.PowerShell.Commands.AddPSSnapinCommand
Would you know how to overcome this issue?
Thank you!
Hi Carlos,
did you install WebDeploy?
Hi, Thanks for the details, and it was informative. Do you have any architecture diagram for Uipath PaaS implementation with WAF. Please share. Thanks
All the best
Vinod
Hi Vinod,
at this point I did not implement WAF in front of UiPath service. I suspect it should not be hard and it would be very similar to deploying WAF in front of any web app. Check out this great MS resource
Hello Frank,
Thank you so much for writing this in the blog. All this knowledge is essential to be passed on and I appreciate you for that. I have one question – what you see as the biggest difference between deploying UiPath Orchestrator as a Paas vs creating a VM from scratch and installing SQL Server and Orchestrator on the VMs? Other than Paas taking lesser time to deploy.(I did Paas steps in 2 mins and it was pretty straightforward). I also see that there is very less configuration possible when deploying Paas.
Hi Santosh,
PaaS is preferred and recommended way to go if you are going in cloud. Main difference as you also noticed is level of control you have on your environment. Personally, I would always go with PaaS whenever possible.
Good information. Thanks for making such blogs.